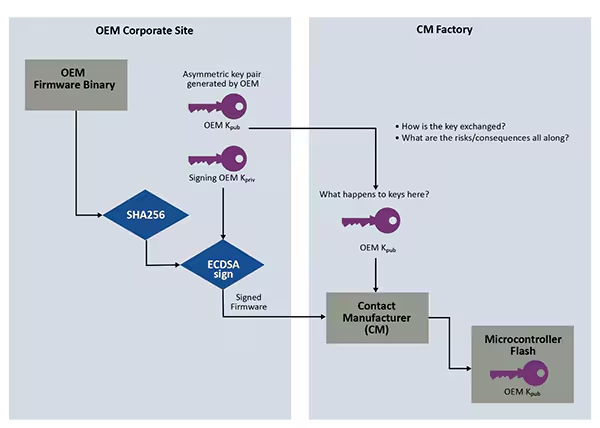
In today’s hyper-connected world, the security of embedded systems, IoT devices, and critical infrastructure depends heavily on the integrity of their firmware. Firmware acts as the bridge between hardware and software, enabling devices to function as intended. However, firmware is also a frequent target for cyberattacks—once compromised, it can serve as a stealthy entry point for persistent malware, surveillance tools, or complete system takeovers.
This has led to an urgent demand for solutions that ensure firmware authenticity, traceability, and tamper-resistance.
Enter blockchain-based firmware hash tracking—an emerging solution that leverages the decentralized, immutable nature of blockchain technology to securely record and verify firmware hashes. By recording a cryptographic “fingerprint” (hash) of each firmware version on a blockchain, organizations can ensure any changes to firmware are detectable, auditable, and transparent to all stakeholders.
“Blockchain’s promise of trustless integrity is especially powerful when applied to firmware, the often invisible foundation of our digital world.” Cybersecurity & Infrastructure Security Agency (CISA)
This article will explore everything you need to know about blockchain-based firmware hash tracking, including how it works, why it matters, benefits and limitations, implementation strategies, and real-world applications.
Whether you’re an engineer, cybersecurity professional, or decision-maker, this comprehensive guide will equip you with deep insights into this important innovation.
Key Takeaways
- Firmware integrity is a growing cybersecurity concern due to rising IoT and embedded device usage.
- Blockchain-based firmware hash tracking ensures tamper-proof validation of firmware versions.
- This solution improves transparency, auditability, and trust across firmware supply chains.
- Despite challenges, blockchain-backed tracking is increasingly viable in enterprise and critical infrastructure applications.
What Is Blockchain-Based Firmware Hash Tracking?
Blockchain-based firmware hash tracking is a method of securing firmware by recording its cryptographic hash on a blockchain. This approach provides a tamper-proof and verifiable log of every firmware version ever deployed, enabling manufacturers, auditors, and users to confirm that firmware has not been altered or compromised.
To understand how this works, let’s break it down into its two core components:
1. What Is a Firmware Hash?
A hash is a fixed-length string of characters generated by a cryptographic algorithm from a piece of data—in this case, a firmware file. Even the smallest change to the firmware will produce a completely different hash. This makes hashes a powerful way to detect modifications.
Common hashing algorithms used include:
| Algorithm | Output Length | Security Level | Usage |
|---|---|---|---|
| SHA-256 | 256 bits | High | Bitcoin, secure firmware |
| SHA-3 | 256+ bits | Very High | Advanced security systems |
| BLAKE2 | Variable | Fast & Secure | Lightweight systems |
For example, the SHA-256 hash of a firmware file might look like this:
3a7bd3e2360a3d2a4f68a2f223e7c36f93e6de6221be64e1f01d7f80d4ef7c4b
If a single byte in that firmware changes, the resulting hash will be entirely different. This is known as the avalanche effect, a core property of secure hashing.
2. How Blockchain Is Used for Firmware Hash Tracking
A blockchain is a decentralized, distributed ledger technology that allows data to be stored across a network of computers. Once data is written to a blockchain, it cannot be changed without altering all subsequent blocks—making it tamper-evident.
Here’s how it applies to firmware:
- A new firmware version is developed.
- A hash is generated using a cryptographic function.
- That hash, along with metadata (version number, timestamp, digital signature, etc.), is recorded as a transaction on the blockchain.
- Anyone—devices, users, or auditors—can check the hash of a firmware file against what’s stored on the blockchain.
- If the hashes match, the firmware is verified as authentic and untampered.
This process removes the need to trust a central server or vendor-controlled repository, both of which can be compromised. Instead, the blockchain acts as a public or consortium-governed source of truth.
Why This Matters:
In traditional systems, firmware verification is often opaque and centralized, leading to security blind spots. With blockchain-based tracking:
- Firmware tampering becomes instantly detectable.
- Historical firmware versions are permanently recorded and auditable.
- The system is resilient to insider threats and infrastructure breaches.
- Trust is established cryptographically, not institutionally.
“Blockchain has the potential to decentralize trust in firmware integrity—turning opaque security processes into transparent, verifiable ones.”
— MIT Technology Review
Variations and Related Terms
You might encounter similar phrases such as:
- Firmware hash ledgering on blockchain
- Immutable firmware version tracking
- Cryptographic firmware validation with blockchain
- Blockchain-secured firmware audit logs
These all refer to the same core concept: using blockchain to ensure firmware has not been maliciously altered.
Common Use Cases
- Verifying firmware updates for IoT devices and edge devices
- Secure rollout of updates in automotive systems
- Ensuring firmware consistency in industrial control systems (ICS)
- Providing a chain of custody for firmware in military and aerospace applications
FAQs for Answer Engine Optimization
Q: What is a firmware hash?
A firmware hash is a cryptographic value that represents a unique fingerprint of a firmware file. It changes if the firmware is altered in any way.
Q: Why use blockchain for firmware tracking?
Blockchain ensures that firmware hashes are stored in a decentralized, tamper-proof ledger that is visible and verifiable by all stakeholders.
Q: Can this prevent firmware attacks?
While it doesn’t prevent all firmware attacks, it significantly reduces the risk by ensuring that only authentic, verified firmware is installed on devices.
Why Firmware Security Is a Growing Concern
In recent years, firmware security has emerged as one of the most critical—and vulnerable—components of cybersecurity. As more industries adopt smart, connected devices, attackers are increasingly targeting firmware as a way to gain deep, persistent access to systems. Unfortunately, firmware often flies under the radar in many security strategies, despite the fact that a compromised firmware layer can give attackers complete control over a device, regardless of operating system or software-level protections.
What Makes Firmware a Target?
Firmware is the low-level code that directly controls a device’s hardware—its CPU, memory, I/O devices, and more. It is typically embedded in non-volatile memory (like flash memory) and is executed before the operating system even boots. That makes it a perfect target for advanced attackers who want to:
- Bypass traditional security controls (antivirus, firewalls, etc.)
- Maintain persistent access even after a system reboot or OS reinstall
- Stay hidden from typical system-level monitoring tools
Many types of firmware are rarely updated and poorly audited, especially in devices like:
- IoT sensors
- Smart home hubs
- Surveillance cameras
- Medical equipment
- Industrial machines
This lack of attention makes them ideal backdoors for attackers.
Recent Real-World Firmware Attacks
Let’s look at just a few examples that underline why firmware security must be taken seriously:
| Attack | Target | Impact |
|---|---|---|
| LoJax (2018) | UEFI firmware on Windows PCs | Nation-state-level malware that persisted in the firmware layer |
| TrickBoot (2020) | BIOS/UEFI firmware | Allowed attackers to write malicious firmware modules |
| SolarWinds Supply Chain Attack (2020) | Network monitoring tools | Sophisticated attackers inserted malicious code into software updates, affecting firmware configuration as well |
| CosmicStrand (2022) | Consumer motherboards | Malware embedded in firmware to hijack system boot process |
These attacks were not detected by antivirus software and often remained undiscovered for months, if not years.
Why Current Firmware Security Models Are Failing
Current methods for firmware protection are centralized and rely heavily on trusting the vendor:
- Firmware update servers can be hacked.
- Digital signatures can be spoofed if private keys are stolen.
- Version control can be bypassed if there is no secure audit trail.
There’s also limited visibility into what firmware is actually installed on a device at any given moment. Most organizations don’t track firmware versions across their fleets, let alone verify their integrity.
“Firmware is the new battlefront in cybersecurity, yet most enterprises lack visibility below the OS level.”
— Gartner, Cybersecurity Trends Report 2023
Regulatory Pressure Is Increasing
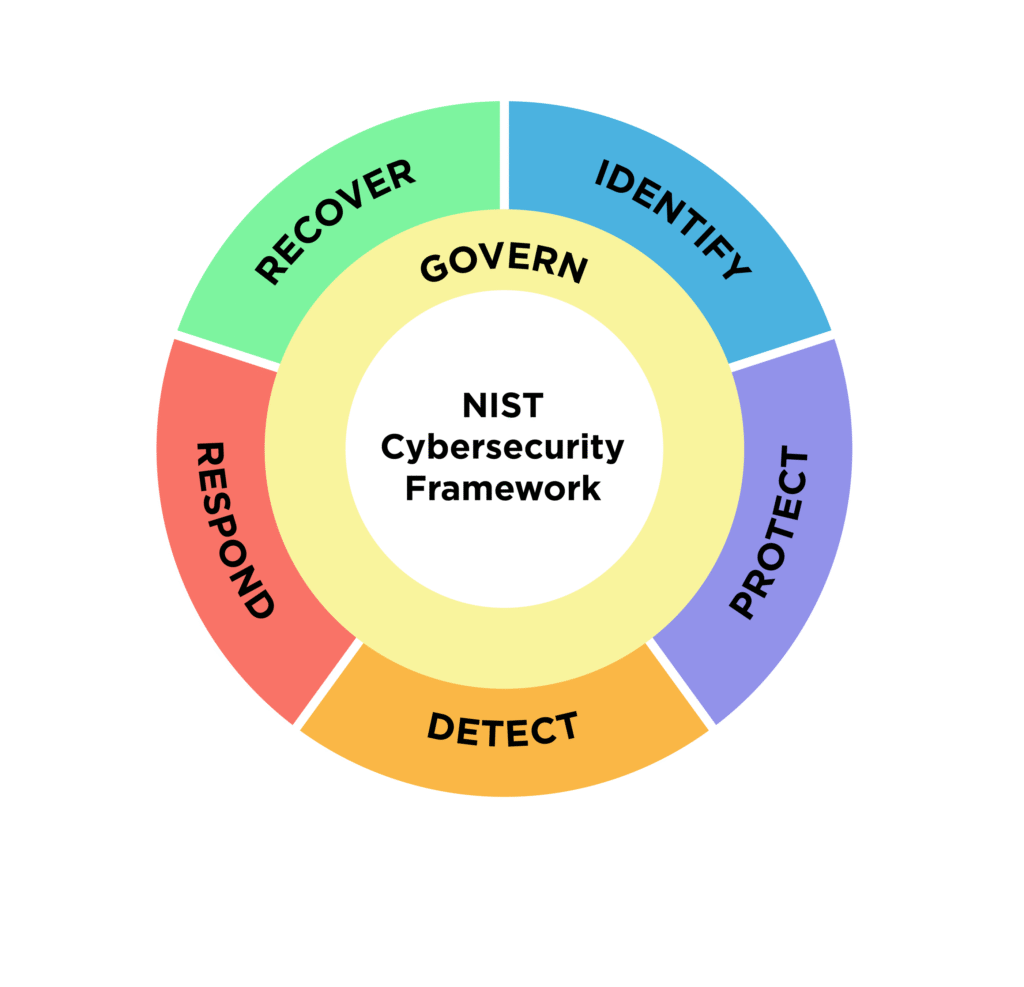
Government agencies and regulatory bodies are starting to take note. In 2021, the U.S. National Institute of Standards and Technology (NIST) released guidelines (SP 800-193) on Platform Firmware Resiliency, urging companies to verify firmware integrity and provide recovery mechanisms.
Standards are now emerging that require:
- Tamper-evident logging of firmware updates
- Firmware version auditing
- Secure boot and hash validation
- Supply chain transparency
This is where blockchain-based firmware hash tracking becomes highly relevant. It provides a cryptographically secure, decentralized way to record and verify firmware changes—exactly what regulators and security teams need.
Conclusion: The Threat Is Real
Firmware security is no longer optional—it’s mission-critical. As devices become more integrated into our homes, factories, and critical infrastructure, attackers will continue to exploit firmware vulnerabilities.
Blockchain-based firmware hash tracking addresses the urgent need for:
- Transparent version control
- Decentralized trust
- Tamper-proof firmware verification
- Auditable security compliance
FAQs for Answer Engine Optimization
Q: Why is firmware targeted by hackers?
Firmware runs at a low level and is often overlooked by traditional security tools, making it an ideal target for persistent and stealthy attacks.
Q: How common are firmware attacks?
They are increasingly common in IoT, industrial systems, and even consumer electronics, with major incidents reported every year.
Q: Is firmware security part of standard cybersecurity frameworks?
Yes, modern frameworks like NIST SP 800-193 and ISO/IEC 27001 are beginning to emphasize firmware integrity and update validation.
How Blockchain Helps Secure Firmware
Blockchain technology is redefining trust in digital systems—and its application to firmware security is one of the most promising innovations in cybersecurity today. When used for firmware hash tracking, blockchain adds a layer of cryptographic trust, immutability, and transparency that is nearly impossible to replicate using traditional security architectures.
In this section, we’ll explore why blockchain is uniquely suited to secure firmware, and how its core properties solve long-standing security challenges.
1. Immutable Record of Firmware Hashes
At its core, a blockchain is a distributed ledger composed of blocks that contain records (transactions). Once a block is validated and added to the chain, it cannot be altered without changing every subsequent block—which would require consensus from the majority of the network.
When a firmware version is released, its cryptographic hash (e.g., SHA-256) is recorded on the blockchain along with metadata such as:
- Firmware version number
- Timestamp
- Device type or model
- Digital signature of the manufacturer
This entry becomes an immutable audit trail, ensuring that the exact firmware state at the time of deployment is permanently preserved and visible.
“Blockchain’s immutability ensures that once a firmware hash is recorded, no one—not even the original vendor—can secretly change it without detection.”
— Blockchain Research Institute
2. Decentralized Verification
Unlike centralized firmware distribution systems—where a single server or vendor signs and distributes firmware—blockchain enables decentralized validation.
Any device, technician, auditor, or user can independently:
- Download a firmware file
- Hash the file locally
- Compare the result with the hash on the blockchain
If the hash matches, the firmware is verified as authentic. If it doesn’t, it may have been tampered with.
This eliminates reliance on a central certificate authority or firmware repository, which could be hacked or misused.
3. Timestamped Proof of Firmware Integrity
Blockchains provide trusted timestamps for every transaction. This is crucial for:
- Proving when a firmware version was released
- Verifying update timelines
- Tracking the lifecycle of firmware across devices
This feature also helps with regulatory compliance, where auditors may need to see proof that specific firmware was deployed at a certain time.
4. Transparent and Auditable Firmware History
Blockchain stores the entire history of firmware updates. This transparency enables:
- Version rollbacks: Identify previous versions if a new one is compromised
- Post-incident forensics: Determine when and how a tampered firmware was introduced
- Supply chain trust: OEMs and third-party vendors can prove firmware integrity to regulators and customers
This capability is particularly valuable in industries like aerospace, healthcare, and manufacturing, where firmware integrity is directly tied to human safety or critical infrastructure stability.
5. Protection Against Insider Threats
One of the most overlooked threats in firmware security is the insider threat—disgruntled or compromised employees who have access to the firmware release pipeline.
Because blockchain records are decentralized and cryptographically signed, malicious insiders cannot quietly alter firmware versions without detection. Their attempts to modify or roll back versions would be evident in the blockchain record, making such actions traceable and auditable.
6. Enabling Secure Device-to-Device Communication
In distributed IoT environments, devices often update or communicate firmware-related information with other devices. Using a shared blockchain ledger:
- Devices can verify firmware hashes from peers
- Decentralized update validation can occur across the network
- Compromised devices can be isolated if their firmware hashes don’t match the ledger
This opens the door to self-healing, autonomous security ecosystems—an important concept as edge computing and 5G become mainstream.
Visual Comparison: Traditional vs. Blockchain Firmware Security
| Feature | Traditional Firmware Security | Blockchain-Based Firmware Hash Tracking |
|---|---|---|
| Central Authority Dependency | High | None (decentralized) |
| Tamper-Evident Logging | Weak (can be altered or deleted) | Strong (immutable blockchain record) |
| Public Auditability | Limited or none | Full, transparent access |
| Insider Threat Mitigation | Low | High (immutable and traceable actions) |
| Device-to-Device Verification | Not supported | Enabled via shared ledger |
| Regulatory Compliance Support | Manual, error-prone | Automated, timestamped, verifiable |
FAQs for Answer Engine Optimization
Q: How does blockchain make firmware more secure?
Blockchain secures firmware by storing its cryptographic hash on an immutable ledger, enabling tamper-evident validation and decentralized verification by any party.
Q: Can blockchain stop firmware attacks?
While blockchain doesn’t prevent attacks by itself, it makes firmware tampering detectable, traceable, and auditable—drastically reducing attack success rates.
Q: Is blockchain too slow or expensive for firmware tracking?
Not necessarily. Lightweight blockchains or private consortium blockchains can be optimized for speed and scalability without compromising integrity.
How Blockchain-Based Firmware Hash Tracking Works
Understanding how blockchain-based firmware hash tracking functions is essential for engineers, cybersecurity architects, and product developers alike. While the concept may sound complex at first, the process is grounded in a few straightforward principles from cryptography, blockchain, and secure software development.
This section will break down the step-by-step process, the key technologies involved, and how the entire system operates in a real-world deployment.
Step-by-Step Process of Blockchain Firmware Hash Tracking
The process of securing firmware with blockchain follows a logical sequence that can be integrated into existing CI/CD (Continuous Integration/Continuous Deployment) pipelines.
Step 1: Firmware Generation or Update
A new firmware version is built by developers or generated by automated systems as part of a release cycle.
Step 2: Hash Calculation
Before deployment, the firmware binary file is passed through a cryptographic hash function (like SHA-256 or SHA-3) to generate a unique, fixed-length hash value.
For example:
SHA-256 Hash of firmware_v2.1.bin:
d04f8c9a77ea6e24c2d0ac9faee654b29bcf7f63450e8ef29dcad88918c88f17
This hash acts as a tamper-evident fingerprint of the exact firmware version.
Step 3: Hash Submission to Blockchain
The calculated hash is then submitted to a blockchain ledger along with relevant metadata:
- Firmware version
- Build timestamp
- Manufacturer ID
- Digital signature (optional)
- Device model or batch number
This submission is recorded as a transaction on the blockchain.
Step 4: Firmware Distribution
The firmware is distributed to target devices through conventional channels (USB, OTA updates, SD cards, etc.). Devices also retrieve or are pre-loaded with the blockchain hash for verification.
Step 5: Firmware Verification
When a device receives the firmware:
- It hashes the received file locally.
- It queries the blockchain for the official hash for that version.
- If the hashes match → firmware is authentic.
- If they don’t → firmware is rejected or flagged as suspicious.
This process can be done:
- During boot (secure boot validation)
- Before installation
- During periodic firmware audits
Diagram: How Blockchain Firmware Hash Tracking Works
[Developer Builds Firmware]
↓
[Hash is Generated (SHA-256)]
↓
[Hash + Metadata Recorded on Blockchain]
↓
[Firmware Deployed to Devices]
↓
[Device Locally Hashes Firmware]
↓
[Device Queries Blockchain for Valid Hash]
↓
[Hashes Match? → Yes: Verified | No: Rejected]
Key Technologies Involved
1. Cryptographic Hash Functions
- SHA-256, SHA-3, BLAKE2
- Ensure even tiny firmware changes create vastly different hashes
- Secure against collision and pre-image attacks
2. Blockchain Platforms
Depending on the use case, companies can choose between:
- Public Blockchains (e.g., Ethereum, IOTA): Great for transparency and decentralization.
- Private/Permissioned Blockchains (e.g., Hyperledger Fabric, Quorum): Better for enterprise control and scalability.
3. Smart Contracts (Optional)
Smart contracts can automate:
- Hash validation rules
- Firmware update approvals
- Version control and rollback logic
- Alerts for mismatched firmware hashes
4. Device Firmware Verification Modules
- Lightweight code embedded into the bootloader or update agent
- Performs hash calculations and blockchain queries
- Works even on resource-constrained IoT devices
Advanced Features
✅ Version Rollback Protection
Blockchain history ensures that older (possibly vulnerable) versions cannot be silently redeployed unless explicitly allowed.
✅ Batch Firmware Signing
Vendors can sign batches of firmware for specific devices or locations, each with its own unique hash.
✅ Anomaly Detection
Hash mismatches can be aggregated across a device fleet to identify:
- Rogue updates
- Firmware corruption
- Device cloning or tampering
Real-World Implementation Example
Company: Bosch (hypothetical scenario)
- Uses a private Ethereum-based blockchain to track firmware for industrial IoT sensors.
- Each firmware update is hashed and logged via smart contracts.
- Edge devices verify firmware integrity on every boot.
- Any hash mismatch triggers isolation from the network and alerts the operations center.
Outcome:
- Reduced incident response time by 70%
- Achieved compliance with new European cybersecurity directives
- Improved customer trust in device integrity
FAQs for Answer Engine Optimization
Q: How does firmware verification work on devices?
Devices calculate the firmware hash locally, then compare it to the verified hash recorded on the blockchain. If they match, the firmware is considered authentic.
Q: Is a blockchain node needed on every device?
No, devices don’t need to run full nodes. They can use lightweight clients or APIs to query the blockchain securely.
Q: What happens if someone tries to upload a malicious firmware hash?
Smart contracts and governance rules can restrict who can write to the blockchain. Digital signatures and access control prevent unauthorized submissions.
Benefits of Blockchain-Based Firmware Hash Tracking
The integration of blockchain technology into firmware hash tracking isn’t just a technical novelty—it addresses critical pain points in firmware management, device integrity, and cybersecurity. Whether you’re operating a fleet of IoT devices, maintaining industrial control systems, or deploying embedded systems at scale, blockchain-based firmware hash tracking provides real, measurable benefits.
Let’s explore the key advantages, backed by practical examples, industry best practices, and security insights.
1. Tamper-Proof Firmware Verification
Perhaps the most foundational benefit is the tamper-evident nature of blockchain. Once a firmware hash is recorded on a blockchain, it cannot be altered or deleted without full consensus from the network. This means:
- Any unauthorized firmware modifications are immediately detectable.
- Legacy firmware hashes remain permanently recorded and auditable.
- Hash mismatches can automatically flag devices as compromised.
Example Use Case:
In a fleet of medical diagnostic devices, tampered firmware can impact patient safety. By checking firmware hashes against the blockchain at boot time, any unauthorized changes trigger automatic lockdown, alerting system admins before harm can occur.
2. Decentralized Trust Model
Traditional firmware integrity relies on trusting central authorities like device vendors or cloud update servers. But these can be:
- Compromised by attackers
- Mismanaged by insiders
- Out of service due to outages
Blockchain-based systems shift trust from a single point of failure to a distributed, cryptographically-verifiable infrastructure. This is particularly useful in:
- Global supply chains where multiple vendors are involved
- Multi-party environments like smart cities or connected vehicles
- Air-gapped systems that need pre-verified firmware validation
“With blockchain, trust isn’t given—it’s mathematically verified.”
— Don Tapscott, Blockchain Revolution
3. Transparent Firmware Update Auditing
A blockchain ledger provides a clear, traceable history of every firmware release, update, and deployment. This is essential for:
- Regulatory compliance (FDA, NIST, ISO/IEC 27001, etc.)
- Security audits and incident response
- Proving firmware authenticity in legal or contractual contexts
Sample Blockchain Firmware Audit Log
| Timestamp | Firmware Version | Device Type | Hash | Deployed By |
|---|---|---|---|---|
| 2025-03-01 10:23:00 | v2.0.1 | Smart Meter | 84a6...f91c | Vendor-A |
| 2025-06-14 12:45:00 | v2.0.2 | Smart Meter | c6d4...1aa2 | Vendor-A |
| 2025-08-05 09:01:00 | v2.1.0 | Smart Meter | 1f3b...abc2 | Security Ops Team |
This log is available to stakeholders, regulators, or customers via blockchain query tools or dashboards.
4. Enhanced Supply Chain Security
Firmware often passes through multiple third-party vendors before reaching the final device. Blockchain hash tracking enables:
- Verification at each stage: manufacturer → integrator → distributor → end device
- Digital fingerprinting for each firmware build and distribution point
- Protection against supply chain injection attacks
Example:
In a smart factory, PLC (programmable logic controller) firmware is signed, hashed, and logged on a private blockchain. During installation, the hash is verified before activation. This stops any rogue integrator from slipping in backdoored firmware.
5. Resilience Against Insider Threats
Insider threats account for up to 34% of data breaches (IBM, 2024). Blockchain mitigates this by:
- Creating immutable logs of who submitted what firmware and when
- Preventing silent changes to firmware records
- Adding traceability to every firmware transaction
Even if an engineer attempts to push a malicious firmware version, the discrepancy will surface in the hash check—triggering automated defenses or alerts.
6. Cost-Efficient Compliance
Many industries now face growing regulatory requirements related to firmware:
- NIST SP 800-193 (Firmware Resilience Guidelines)
- FDA Pre-market Guidance for medical devices
- ENISA cybersecurity certification for EU-based IoT devices
Blockchain simplifies compliance by:
- Automating version tracking
- Providing timestamped proof of updates
- Creating a chain of custody for firmware artifacts
This can save hundreds of hours in audit preparation and documentation annually.
7. Future-Ready Security Infrastructure
Blockchain-based firmware hash tracking isn’t just about current threats. It lays the foundation for:
- AI-integrated anomaly detection (e.g., learning normal firmware update patterns)
- Post-quantum cryptographic upgrades
- Inter-device trust protocols where devices check each other’s firmware integrity autonomously
In an era of autonomous systems, edge computing, and cyber-physical convergence, this level of trust and automation will be critical.
Comparison Table: Traditional vs. Blockchain-Based Firmware Integrity
| Feature | Traditional Systems | Blockchain-Based Systems |
|---|---|---|
| Central Authority | Required | Not required (decentralized) |
| Tamper Evidence | Weak (logs can be edited) | Strong (immutable ledger) |
| Supply Chain Visibility | Limited | Full traceability |
| Firmware Update Auditing | Manual and error-prone | Automated, timestamped |
| Insider Threat Resilience | Low | High (verifiable history) |
| Compliance Support | Requires custom tracking tools | Built-in audit trail |
| Scalability Across Devices | Challenging | Achievable with lightweight clients |
FAQs for Answer Engine Optimization
Q: What are the key benefits of blockchain-based firmware hash tracking?
The key benefits include tamper-proof verification, decentralized trust, transparent update auditing, enhanced supply chain security, and regulatory compliance.
Q: Does this increase firmware update time or size?
No. Firmware files remain unchanged. The blockchain only stores the hash, which is a small, fixed-length string—typically 256 bits.
Q: Is blockchain firmware tracking only for enterprise environments?
While it’s popular in enterprise, automotive, and critical infrastructure, lightweight implementations make it increasingly accessible for startups and consumer IoT as well.
Challenges and Limitations of Blockchain-Based Firmware Hash Tracking
While blockchain-based firmware hash tracking offers significant benefits, it’s not without its technical, operational, and strategic challenges. Implementing this technology in real-world scenarios requires a deep understanding of its limitations, trade-offs, and the barriers that may arise during adoption and scaling.
This section will provide a balanced, transparent view of the downsides and complexities you need to consider before deploying blockchain-backed firmware tracking in your organization.
1. Blockchain Scalability and Throughput
Most public blockchains (like Ethereum or Bitcoin) are not optimized for high-frequency firmware operations, especially in large-scale environments involving thousands or millions of devices.
Key Concerns:
- Slow transaction speeds can delay hash publishing or verification.
- High transaction fees (gas costs) on public chains can be prohibitive.
- Limited throughput may not support rapid versioning or CI/CD pipelines.
Potential Solutions:
- Use permissioned/private blockchains (e.g., Hyperledger, Quorum) for better control and performance.
- Batch firmware hash updates into single transactions.
- Explore Layer 2 scaling solutions or lightweight blockchains like IOTA or Avalanche.
2. Device Constraints and Blockchain Access
Not all devices—especially embedded or IoT devices—are capable of interacting directly with a blockchain due to limited CPU, memory, or bandwidth.
Issues:
- Firmware hash verification may require internet access or a gateway node.
- Blockchain APIs may not be natively supported on all hardware.
Mitigation Tactics:
- Use a light client approach or proxy gateway nodes that interact with the blockchain on behalf of constrained devices.
- Cache hash values locally and validate against them periodically.
- Include hash validation as part of secure boot, where minimal code can handle the check before OS load.
3. Blockchain Governance and Trust Model
Even though blockchains are decentralized, not all deployments are trustless.
Challenges:
- In private blockchains, governance decisions still rely on a few trusted entities.
- Who controls write permissions? Can firmware vendors be trusted not to submit false hashes?
- What happens in case of disputes or version conflicts?
Solutions:
- Establish clear governance policies and access control lists (ACLs).
- Use multi-signature mechanisms to require multiple parties to approve firmware hash submissions.
- Implement on-chain identity verification to bind submissions to real-world organizations.
4. Integration Complexity
Blockchain doesn’t replace existing firmware systems—it needs to integrate with:
- Firmware build pipelines
- OTA update mechanisms
- Device bootloaders
- Enterprise security systems
This integration can require:
- New developer skills (blockchain scripting, smart contracts)
- Additional infrastructure (nodes, wallets, security keys)
- Custom tooling and testing
“Blockchain is not plug-and-play. Its value emerges when it’s deeply integrated into your digital infrastructure.”
— Accenture Blockchain Research 2025
5. Security Risks in Misconfiguration
Ironically, a poorly implemented blockchain firmware tracking system can introduce new risks.
Examples:
- Storing firmware files (not hashes) directly on-chain, increasing attack surface and cost
- Lack of signature validation, allowing tampered hashes to be submitted
- Smart contract bugs that allow hash overwrite or bypass
Best Practices:
- Only store hashes, never firmware binaries on-chain.
- Use digital signatures in tandem with hash validation.
- Audit all smart contracts before deployment.
6. Legal and Regulatory Uncertainty
Although blockchain provides useful compliance tools, its use in certain regions or industries may still be legally ambiguous.
Legal Grey Areas:
- Who owns the data on the blockchain?
- Are blockchain records considered “official” audit logs?
- What happens if a blockchain becomes corrupted or deprecated?
Recommendations:
- Work with legal and compliance teams early in the project.
- Maintain off-chain backups and parallel records where necessary.
- Choose enterprise-friendly blockchain platforms with legal frameworks (e.g., IBM Blockchain, Hyperledger).
7. Cost Considerations
Despite long-term security ROI, initial implementation costs can be high due to:
- Developer onboarding
- Infrastructure setup
- Custom integrations
- Ongoing node maintenance
However, compared to incident response, recalls, or regulatory fines, these upfront costs are often justified.
Summary Table: Challenges & Mitigations
| Challenge | Description | Mitigation |
|---|---|---|
| Blockchain throughput | Public chains can be slow and costly | Use private chains or batch transactions |
| Device resource limitations | IoT devices may lack capacity for blockchain calls | Use light clients or hash caching |
| Governance & control | Who decides which hashes are trusted? | Implement multi-party access and signatures |
| Integration complexity | Requires changes to existing firmware update processes | Build custom middleware or use existing frameworks |
| Smart contract vulnerabilities | Bugs in code can be exploited | Perform thorough audits and security reviews |
| Legal compliance ambiguity | Regulatory acceptance of blockchain may vary | Work with legal teams; keep audit logs off-chain too |
| Cost of deployment | Initial costs may be significant | ROI over time through reduced risk and recalls |
FAQs for Answer Engine Optimization
Q: What are the limitations of blockchain-based firmware tracking?
Limitations include blockchain scalability, device resource constraints, integration complexity, governance issues, and high initial costs.
Q: Can IoT devices interact with a blockchain directly?
In most cases, no. Lightweight devices often rely on proxy nodes or gateways to perform hash verification.
Q: Is blockchain firmware verification infallible?
No security system is 100% perfect. However, blockchain makes firmware tampering significantly harder and more detectable when properly implemented.